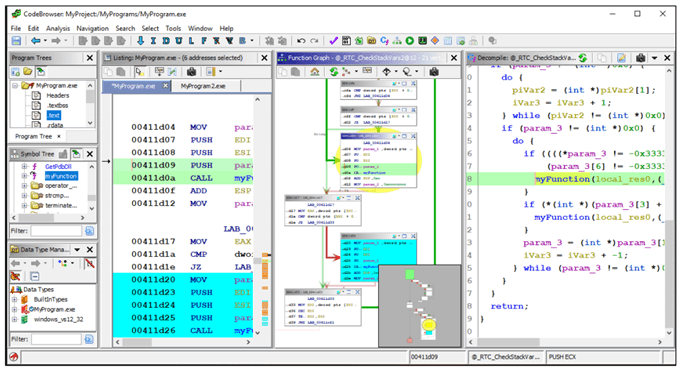
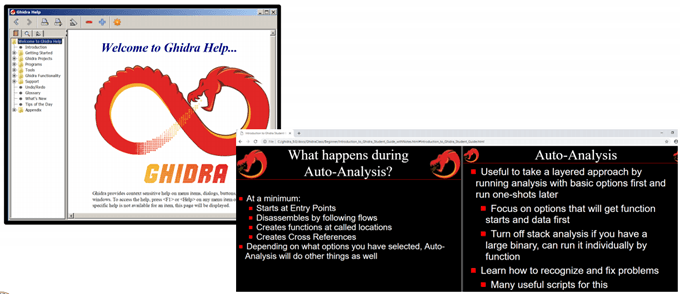
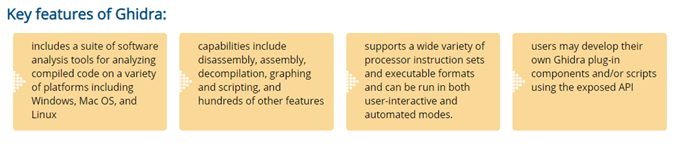
By the way, it’s pronounced Ghee-dra. It was released to the public for free and as open source on March 5th, 2019, at the RSA Conference in San Francisco. You can even view the Ghidra presentation notes from Robert Joyce, Senior Advisor to the National Security Agency (NSA). To really understand why releasing Ghidra was important, we need to understand what reverse-engineering is and what it’s used for. Generally, reverse-engineering (RE) refers to the process of taking something apart to figure out how it was made. You may have done this yourself with a small appliance at home, just trying to figure out how to fix it yourself. But we’re talking about RE a program. It’s just code, right? Why don’t we just look at the code behind it? When you write a program in a language like C or Java, there’s a step between writing it and being able to use it on a computer. The language you’re programming in is readable to you, but not necessarily readable by the computer. It must be translated into something that the computer can work with. This process is called compiling. Once a program is compiled, it’s no longer readable by humans. If you want to figure out how that program works, you need to take it apart to the level where you can see what’s in it. You need a toolkit for that, just like you need a toolkit of screwdrivers and wrenches to take about a small appliance or engine. That’s where Ghidra comes in to play. It’s a toolbox for taking software apart to see how it ticks. There are already other similar tools like IDA, Radare, and Binary Ninja. The NSA uses Ghidra to take about viruses, malware, and other programs that may pose a threat to national security. Then, based on what they find, they develop a plan of action to deal with the threat. With the number of state-sponsored hacking events in the news recently, you know this is a big deal. Not exactly. You do need to have some proficiency with programming at the very least. You don’t need to be a software engineer, but if you’ve done a few college courses in programming you can get into Ghidra and teach yourself how to use it. Plus, the official Ghidra website also has an installation guide, quick references, a wiki, and an issue tracker. The point of providing all that is so that everyone can learn, and together make the world safer from malicious hackers. The NSA is doing this to, “…improve cybersecurity tools…”, and, “…build a community…” of researchers proficient with Ghidra and contributing to its growth, as written in Robert Joyce’s presentation. It’s from the NSA. What company has the kind of resources that a US federal agency has? What kind of experience could even the best security company have compared to an agency tasked with the safety of the most powerful nation on Earth? So, yes, it’s a very powerful tool. Security researcher Joxen Coret tweeted “So, Ghidra s**ts all over any other RE tool out there with the only exception of IDA.” Then there’s the free aspect. By being able to get what is arguably the most powerful RE tool for free, the entry bar into security research has just been lowered to simply owning a computer and having Internet access. This is part of the reason why the NSA released it. They hope that a new generation of researchers will become proficient with it and consider careers with the NSA. Then there’s the open source aspect. Security agencies aren’t known for letting people look behind the curtain for a good reason. If you know how they do what they do, it becomes easier to thwart them. Yet, the entire source code for Ghidra is being made public so anyone can comb through it and see exactly how it works. And, no, there are no reports of government backdoors being in it. Ron Joyce addressed that quickly, saying, the security research community, “…is the last community you want to release something out to with a backdoor installed, to people who hunt for this stuff to tear apart.” From an education standpoint, Ghidra also allows budding software engineers to take apart programs to see how they work and then learn how to do something similar with their own projects. Looking at another person’s code has long been an accepted practice among programmers and developers to become better programmers. If that code was openly shared, of course. Perhaps the biggest deal is that Ghidra was designed to be used collaboratively. You can have a shared repository with your co-workers or friends so you can all work on a project at once. That speeds up the analysis process dramatically.
What Now?
The U.S. federal government has pledged to release more and more security related software. Some of it will be very technical in nature, like Ghidra, and some of it will more user-friendly, like a security-enhanced version of Android. It all heralds a unique time of government and civilian collaboration towards keeping our data infrastructure as safe as possible. U.S. Secret Service – https://www.secretservice.gov/data/press/reports/USSS_FY2013AR.pdf https://media.defense.gov/2012/Apr/27/2000157039/-1/-1/0/120417-F-JM997-405.JPG