That broad range of functionalities come with vulnerabilities as well. Hackers are often able to access the code and infect WordPress sites with malware just as they might plant malware on a router. Malware can infect and destroy your site, so it’s important to act quickly to remove malware from your WordPress site.
Contact Your Web Host First
Before attempting any of the suggestions below, contact your hosting company first. It is possible that the host server, especially if you are on a shared server, is spreading malicious code from another site onto yours. Ask them to do a scan of their server to ensure it is not the culprit before attempting to remove the malware from your own site. In addition, they can make suggestions to less technical website owners on how to safely scan and remove malware from their site. Some hosts might also offer services where they will remove it for you. And then backup your site, reducing the risk of carrying the malware into your backup. Web hosts have the expertise, tools, and options to deal with malware, so check with them first before attempting to do it on your own.
Take Preventative Measures
It’s always better to try to prevent threats before they happen. The most crucial action users should take is to make sure they are always running the latest and most stable version of WordPress, even if they are only installing on a test version on their computer. Newer versions are usually released to fix common vulnerabilities found in previous versions. The same is true for plugins and themes. Keep them up-to-date and remove those you aren’t using. Some of the many negative issues that malware can cause on a WordPress site include:
Web and MySQL increased consumption of server resources.Unwanted advertising.Spam mail sent in bulk.Theft of customers’ and users’ personal data.Loss of information from your site.Google penalties.
What can you do if your website is infected or hacked? In this article, we will outline the steps you can take to remove malware from a WordPress site.
Use WordPress Malware Removal Plugins
If you can log in and access your WP admin area, you may not have to reload your entire site. Using a suitable WordPress plugin may help remove malware from your WordPress website.
MalCare Security
MalCare is a premium plugin that will instantly remove malware from your WP installation. Not only will it clean up a hacked site, but it will also protect against future security breaches. One of the many benefits of MalCare is that it scans your site on its own servers. Your website will not experience any load on its resources and will continue to run smoothly. There are four pricing levels starting at $99/year for one site (Personal) up to a Custom Agency Plus plan for more than 20 sites. Malcare is a comprehensive WP security plugin that includes many additional features such as:
Real-time email alerts.Tracking small file changes.Minimizing false alarms.
WordFence
One of the most used plugins for WP security is WordFence. It includes a malware scanner and endpoint firewall. From protection against brute force attacks to firewall blocks, the free version of WordFence is powerful enough for smaller websites. If you want additional features such as two-factor authentication, leaked password protection, and advanced manual blocking, you can purchase a premium license. The pricing is based on the number of licenses you buy, starting at $99 for one.
All in One WP Security & Firewall
One of the free security plugins with the most features is All in One WP Security & Firewall. It provides an easy visual interface using meters and graphs. The plugin is designed for beginners and more advanced developers with its three categories: basic, intermediate, and advanced. All in One WP Security will protect websites by:
Providing file and database security.Enhancing user registration security.Blocking forceful login attempts.
Additional features include the ability to back up .wp-config and .htaccess files. Users can also restore these files if anything goes wrong on their site. For a full list of all WordPress security plugins, visit WordPress.org. If you are unable to log in, you may have to reinstall your entire site. If you are more tech savvy, and run a site on your own server, carefully follow the steps below. Keep in mind that backing up your site and erasing it can be dangerous and should only be attempted by highly technical web owners.
Backup Your Database & All Files
If you’re infected and need to remove malware from your WordPress site, it’s important to protect your content immediately. Before doing anything, make a complete backup of your WordPress site so you can restore it in case anything goes wrong. Be sure to back up a clean version of your MySQL database and FTP account. There are several ways to back up a site, including via cPanel, phpMyAdmin, and WordPress plugins (such as Vaultpress). It is highly recommended that all WordPress users backup their site regularly. The steps below outline how to manually remove malware from your WordPress site.
Step 1: Examine Your Files
After you have backed up your entire WP site, download the backup zip file on your computer. Open it by left double-clicking on it. You should see the following files:
All core WordPress files.Wp-config.php..htaccess: This is a hidden file and includes the name, username, and password to your WordPress database. To make sure you backed this file up, use a code editing application or an FTP program that allows you to view hidden files. Be sure to check the Show Hidden Files option.The wp-content folder that includes themes, plugins, and uploads.SQL database.
Step 2: Erase All Files & Folders From The Public_html Folder
When you are sure you have a complete backup of your website, go into your web hosting File Manager. Find the public_html folder and delete its contents except for wp-config.php, wp-content, and cgi-bin folders. Make sure you are viewing the invisible files too, including .htaccess as it may be compromised. If you are hosting multiple sites, you should assume they have also been compromised because cross-infection is common. Follow the same process for all hosted sites on the same server. Open the wp-config.php file and compare it against a sample wp-config file. You can find this file in the WP GitHub repository. Also, look through your file to see if anything looks suspicious such as long strings of code. If you are sure something should not be there, remove it. Now go to the wp-content directory and:
Make a list of all your installed plugins and then delete them.Delete all themes, including the one you are using. You will reinstall it later.Look in your uploads folder to see if there is anything in it that you didn’t put there.Delete index.php after you have deleted all the plugins.
Step 3: Install a Clean Version Of WordPress
Navigate to your web host control panel and reinstall WordPress into the same directory of the original location. It will either be the public_html directory or in a subdirectory if you installed WordPress on an add-on domain. Use the one-click installer or QuickInstall (depending upon your hosting company) in your web hosting control panel. Unzip the tar or zipped file and upload your files to your server. You will need to create a new wp-config.php file and enter the data from your website backup. You only need to enter the database name, password, and prefix.
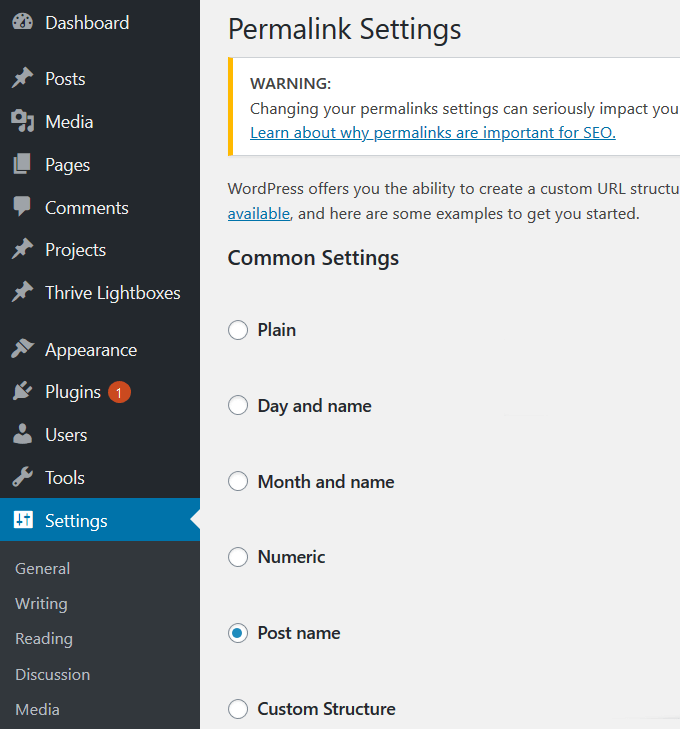
Step 4: Reset Permalinks & Passwords
Log into your WP site and reset all usernames and passwords. If there are any unrecognized users, it means your database has been compromised. You can hire a professional to clean up your database to remove any malicious code. To reset Permalinks, go to Settings > Permalinks and then Save Changes. This process will restore the .htaccess file and fix your site URLs so they will work. Also, reset all hosting accounts and FTP passwords.
Step 5: Reinstall Theme & Plugins
Don’t install old versions of your theme or plugins. Instead, get new downloads from the WordPress repository or the premium plugin developer’s site. Don’t use plugins that are no longer supported. If you have customizations from your old site theme, look at the backup files you downloaded to your computer and replicate the changes on the fresh copy.
Step 6: Scan & Re-Upload Your Images & Documents From Your Backup
This step can be tedious, but it is necessary. Carefully look through your images and uploaded files before you copy them back into the new wp-content > uploads folder in the file manager. Use an up-to-date antivirus program to scan all the files to see if any of them are infected. Upload the clean files back to your server using an FTP client or the file manager. Keep the folder structure the same so you don’t end up with broken links.
Step 7: Notify Google
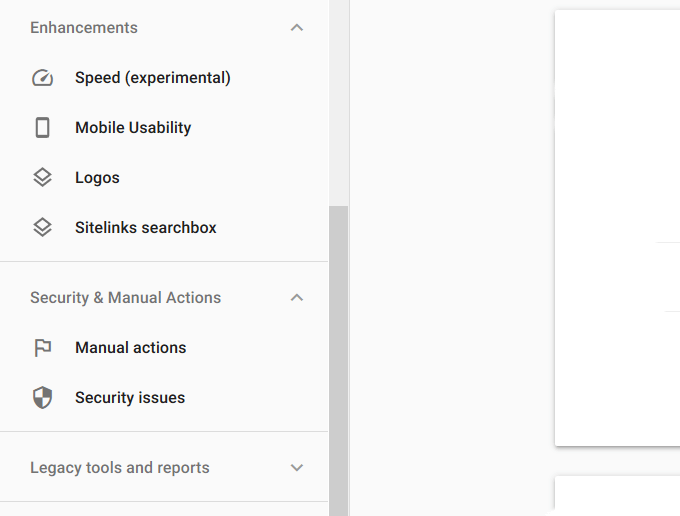
If you found out that your site was compromised by a warning from Google, you need to let them know that you have removed the malware so they can dismiss the notice on your account. Go to Google Search Console and log in if you already have an account. If you don’t, register your website. Find Security & Manual Actions in the left-hand navigation. Click the dropdown and select Security Issues. Here you will see a report about your site’s security. Choose Request a review and submit it to Google.