Now there are two ways to manage Cisco switches: from the web-based GUI interface or from the terminal-based command line interface. I have found that the web-based GUI is not nearly as stable as the Cisco IOS available from the CLI. On several occasions, after trying to save a configuration change on the GUI, the entire switch crashed and I had to reboot it in order to access the GUI again. If you’re going to use the CLI, though, you’ll first need to enable SSH access on the switch. In this article, I’m going to talk about how you can turn on the SSH service and login using the username and password stored in the local database. In my next article, I’m going to talk about how you can make the login process even more secure by using public and private keys to establish the SSH session rather than just a username and password.
Enable SSH Service
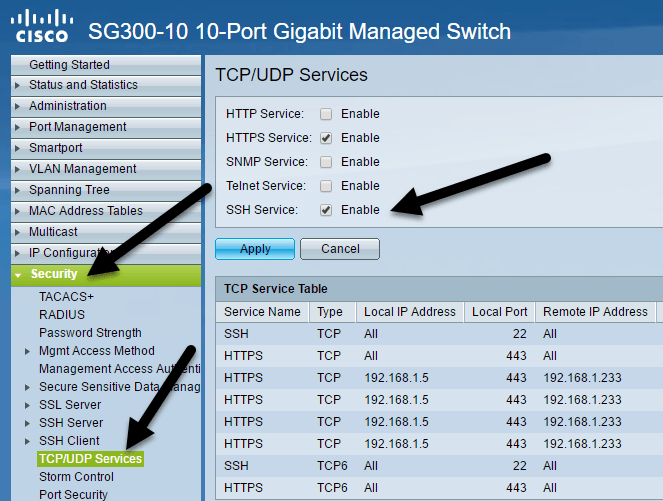
The first thing we need to do is enable the SSH service on the switch. I’m going to show you how to do this using the web-based interface as that was easier for me than connecting to the switch using the console port.
Once you are logged in, expand Security in the left-hand menu, then click on TCP/UDP Services. On the right-hand pane, you’ll see the different TCP and UDP services you can enable for your Cisco switch. In my case, I already had HTTPS checked, so I went ahead and checked SSH Service also. Make sure you click the Apply button to save the changes. Note that this will only save the change to running config. If you want the change to persist even after rebooting the switch, you’ll need to copy the running config over to startup config. The web GUI is usually good at reminding you about this by flashing an icon in the top right corner of the screen.
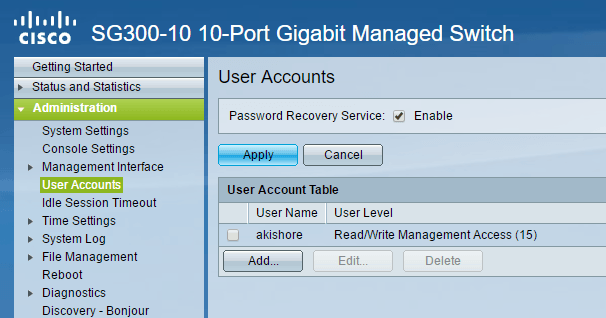
That’s about all you must do to enable basic SSH on your switch. So which user can log into the switch? Well, you can see the list of users by expanding Administration and then clicking on User Accounts.
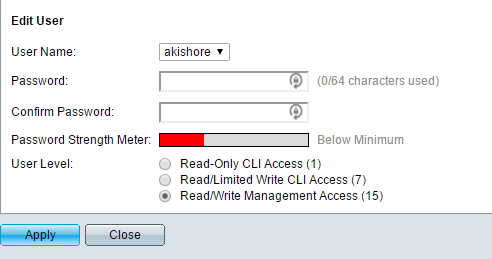
Here you will see the list of accounts that can log into the switch. Note that the user accounts listed here can be used to log into the web-based GUI and the CLI via SSH. In the example above, you can see that I only have one account and the User Level is Read/Write Management Access. There are also other user levels and you may want to create another user account specifically for accessing the switch via SSH with limited write access. You can do this by adding a user and then choosing the appropriate user level for that account.
If you choose Read/Limited Write CLI Access, the user cannot access the switch via the GUI interface and can only access some CLI commands.
Use puTTY to SSH into Switch
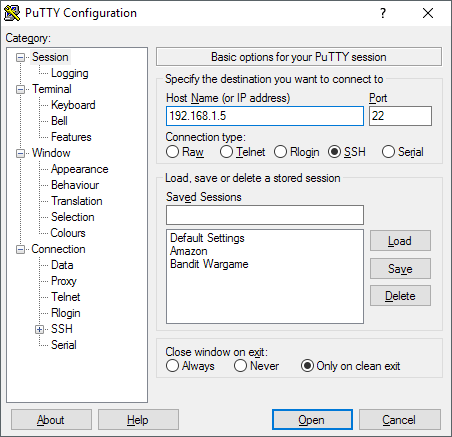
Now all you have to do is use your favorite SSH client to log into the switch. I use puTTY and will use that for any examples. Open puTTY and enter the IP address for your switch. Make sure SSH is selected and you should be good to go.
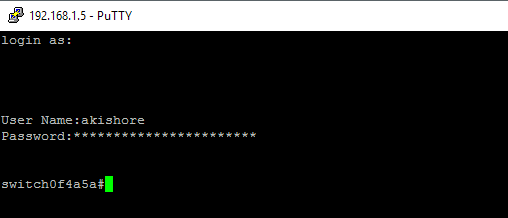
You’ll first see a prompt that says login as, which you can just ignore by pressing Enter.
Then you’ll get a prompt for the User Name. Type in the username for the account you setup and then enter the password. If all works well, you should get the switch prompt. In my case, my account has full access and control, so I automatically start in privileged EXEC mode. That’s probably not a good idea, so it’s best to create an account with less access and then setup an Enable mode password. I’ll talk about how to do that also in a future post. If you have any questions or ran into problems enabling SSH on your Cisco switch, post a comment and I’ll try to help. Enjoy!